On this blog, I would like to share out some simple knowledge on how to stop and fix the virus.
Let us take some example: flash.10.exe and macromedia.10.exe is one of the virus I infected before which it's normally spread via removable devices like pendrive.
Basically, the common behavior that the virus normally will do is to disable three important features inside our machine.
- Folder Option
- Regedit
- Task Manager
Once infected by this kind of virus, you will no longer able to use those features mentioned above. No worries!!!
How we going to trace the viruses since the useful features has been disable?
Firstly, what we need to do is to enable back our Regedit. How to know it's already been disable?
Run -> Type regedit, then you should see something like screenshot below.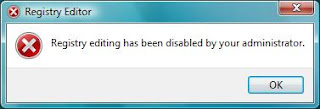
So, follow the steps below to enable your regedit:
- Run gpedit.msc (must have administrator privileges)
- Navigate "User Configuration\Administrative Templates\System"
- Go to "Prevent Access to Registry Editing Tools"
- "Disable" it if the current status is "not configured" or "enable"
Once done, you will allow to use back your regedit.
Secondly, what we need to do is to recover back our Folder Option on Explorer Toolbar. The Folder Option is important for us to enable and disable features like "Show Hidden Files and Folders" and "Hide Protected Operating System Files (Recommended)". Since the Folder Option already disable, how you going to use it? Simple...
For those who don't know where is the Folder Option located:
Screenshot below is the one that has been disable, so you will not see it inside Toolbar.
- Run regedit (must have administrator privileges)
- Navigate "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer"
- Create "NoFolderOptions" using DWORD (32bit value). 1 to enable and 0 to disable
- Reboot
or
- Run gpedit.msc (must have administrator privileges)
- Navigate "User Configuration\Administrative Templates\Windows Components\Windows Explorer"
- Go to "Removes the Folder Option menu item from the tools menu"
- "Disable" it if the current status is "not configured" or "enable"
You will have your Folder Option recover after reboot.
Lastly, to enable task manager that use to view running processes and services.
How to know it's already been disable?
Run -> Type taskmgr, then you should see something like screenshot below.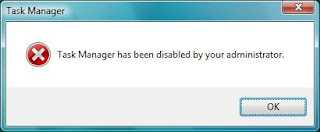
Follow the steps to get it enabled:
- Run regedit (must have administrator privileges)
- Navigate "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System"
- Create "DisableTaskMgr" using DWORD (32bit value). 1 to enable and 0 to disable
- Reboot
or
- Run gpedit.msc (must have administrator privileges)
- Navigate "User Configuration\Administrative Templates\System\Ctrl+Alt+Del Options"
- Go to "Remove task Manager"
- "Disable" it if the current status is "not configured" or "enable"
Once you enabled all the features that we need. Then is time to find the virus...
- Go to Folder Option -> view, radio button on "Show hidden Files and folders" and unchecked "Hide Protected Operating System Files (Recommended)"
- Go to your pendrive (if the main source spread from your pendrive), check is there any suspicious file hidden. Normally contain one executable (.exe) file, 1 autoexec file or .inf file or .vbs file presence. Please be aware of this.
- Is advisable to check the content inside the inf or vbs file (cause it might contains some useful information on how it runs the virus) by using notepad.
- Just recently, my machine get infected by one virus called KB915865.exe via my pendrive. After I unhide the file, it contain 1 folder named MSOCache and 1 inf file. When you open the file with notepad, it will show something as below:
[AutoRun]
open=.\MSOCache\90000804-6000-11D3-8CFE-0150048383C9\KB915865.exe
shellexecute=.\MSOCache\90000804-6000-11D3-8CFE-0150048383C9\KB915865.exe
shell\AutoOpen\command=.\MSOCache\90000804-6000-11D3-8CFE-0150048383C9\KB915865.exe
shell=AutoOpen
- Base on the script, you will notice that it will perforn autorun once you plug in you devices. Hence, open your regedit, search for KB915865.exe. From your search, you will find out something as below:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{d0233621-5515-11dc-9b8a-00116b31ca63}]"BaseClass"="Drive"
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{d0233621-5515-11dc-9b8a-00116b31ca63}\shell]@="None"
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{d0233621-5515-11dc-9b8a-00116b31ca63}\shell\Autoplay]"MUIVerb"="@shell32.dll,-8507"
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{d0233621-5515-11dc-9b8a-00116b31ca63}\shell\Autoplay\DropTarget]"CLSID"="{F26A669A-BCBB-4E37-ABF9-7325DA15F931}"
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\{d0233621-5515-11dc-9b8a-00116b31ca63}\shell\AutoRun]@="Install or run program""SetWorkingDirectoryFromTarget"="""ShellExecute"="KB915865.exe"
Notes: Different machine will have different ID ({d0233621-5515-11dc-9b8a-00116b31ca63})
- Delete it. But bare in mind, this virus is strong enough to auto generated itself each time you plug in your pendrive even though you have formatted your pendrive for n of time.
- Reason is the virus in earlier stage already copied some files into your machine without your acknowledgement.
- To confirm the truth, run msconfig -> Startup tab -> check is there any suspicious system run during startup.
- For this case, I found out that my machine startup "userinit" item in C:\Windows\System32\cologsver.exe which I found out to be a problematic file which always auto-generated the virus file inside my pendrive no matter how many times i formatted.
- Hence, disable the item -> reboot -> go to C:\Windows\System32 to delete "cologsver.exe". Or delete the entry "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Cologsver.exe" from your registry.
- Solved. Repeat the steps above if you worried that the virus still remain inside your machine.
Important notes:
- The finding and solution provided will not guarentee your machine 100% clean from viruses. It's only my own finding, solution and experience. Use at your own risk!!!
- Please use the registry wisely as it will cause a serious damage to your machine Operating System and setting.
- Please back up your data 1st.
- Solution provided is only apply to certain virus, it may not apply to other viruses.
- If you encounter any other strong viruses, you are recommended to consult your senior, use trusted anti-virus or worst come to worst, format your machine immediately.
C&C are welcome. Please let me know if you unclear of certain steps provided.
Thanks for reading this blog.
No comments:
Post a Comment